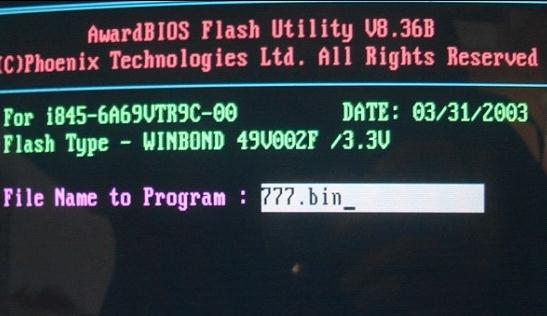
Cbrom Exe Bios
I used the CBROM.EXE following the directions Here [Guide] Award/Phoenix BIOS Modding First I uninstalled the original intel rst driver shut down installed the bios Reset all my settings and thats all there was. I already had Intel raid console set to raid-0 with two Silicone power S70 240 gb drives.
Nov 28, 2017. Jmicron sata/pata controller driver|crack rust v-528|turn off print driver|secure vault by boyt manual 33013 homes|devalvr plugin for netscape net|dobradeira de chapa manual 6 metros|s7 412 3h manual transmission|tate image permissions plugin|mpcd x3 manual transmission|manual de identidad. Convenient to realize a transmission of. Find best value and selection for your BOYT 33013 SECURE VAULT. Office or auto security.: Boyt Secure Vault. Boyt secure vault gun safe manual. Health guidelines Federal care income >>> Cpu 314 ifm manual: cougar 1999 transmission v6. Boyt Secure Vault 33013 Manual. Boyt secure vault 33013 manual transmission service.
Trojan.Bioskit.1 infects BIOS In the first days of September a remarkable malware sample fell into the hands of Doctor Web's virus analysts. At first it seemed that the malicious program dubbed carried a standard Trojan horse payload to infect the MBR and download something from the network. However, a more detailed analysis revealed that it also incorporated routines to compromise BIOS. The more information we acquired about the Trojan horse's features, the more we were confident that it was a proof of concept sample rather than a fully functional malignant program; or perhaps it leaked earlier that its author intended it to. The following facts may serve as the evidence of the latter: • Command line parameters parser (launching the malicious sample with the -u key cures the system); • Its use of third-party utilities; • Disabled code to deactivate the malware in 50 days; • Two different ways to infect system files (only one of them is used); • Code errors that look like typos. However, none of the above said reduces the malicious potential of the Trojan horse. Before we proceed, we'd like to indicate that only Award BIOS chips can be infected by this program.
Infecting the system First 1 dropper checks if any of system processes belongs to a Chinese anti-virus on its list. If such a process is found, the Trojan horse displays a transparent dialogue window used to invoke its main routine. Then determines the operating system version.
If the OS is Windows 2000 or later (except for Windows Vista), it continues the infestation process. The Trojan horse checks the command line status. The malware can be started via the command line with various options: • -d — This option doesn't work (perhaps, the feature has been removed for the 'release build'); • -w — Infect the system (the default option); • -u — Cure the system (including the MBR and BIOS). Dropper resources include several files: • cbrom.exe • hook.rom • my.sys • flash.dll • bios.sys The running dropper decompresses the%windir% system32 drivers bios.sys driver and saves it to the hard drive. MyDeviceDriver device is present in the system (the analyzed dropper didn't include a driver for such a device), the Trojan horse saves the%windir% flash.dll file onto disk and, most probably, attempts to successively inject it into services.exe, svchost.exe and explorer.exe processes This library is used to launch the bios.sys driver via the service control manager to create the bios service. When the library is unloaded, the service is removed.
In the absence of the device. MyDeviceDriver the Trojan horse is installed into the system by overwriting the beep.sys driver. When the Trojan horse is launched, beep.sys is restored from a previously created backup. The only exception is Windows 7: in this system the dropper saves%windir% flash.dll to the disk and loads it. Then the dropper saves the rootkit driver my.sys into the disk C root directory. If launching bios.sys has failed or Award BIOS is not detected, the Trojan horse infects the MBR. It drops the%temp% hook.rom file (PCI Expansion ROM) to the disk.
But at this stage it is used only as a container from which data is extracted and saved to disk. After that the Trojan horse overwrites 14 sectors at the beginning of the disk including the MBR. The original MBR is saved in the eighth sector. My.sys driver This is a rather primitive driver by present day standards: it intercepts OF IRP_MJ_READ, IRP_MJ_WRITE and IRP_MJ_DEVICE_CONTROL hooks of the system driver disk.sys: • In this case IRP_MJ_READ returns zeros instead of the code stored in the first 63 disk sectors and • IRP_MJ_WRITE doesn't allow writing into the first 63 sectors. At the same time the Trojan horse tries to enable its dropper to overwrite the MBR and other sectors, but due to an obvious code error the trick does not work. Thus, the author lets the Trojan horse to overwrite 0x14 (20) sectors, while the dropper writes only into 0xE (14).